Vulnerability Management
Purpose
The University of New Mexico is committed to protecting information with which it is entrusted. This component of the UNM Information Security Program aligns with the National Institute of Standards and Technology (NIST) Special Publication (SP) Series and Frameworks. This Vulnerability Management program component is responsible for describing how UNM will help minimize risk to the confidentiality, integrity, or availability of information for which UNM is responsible. This Vulnerability Management program component accomplishes this by providing UNM with a standard and consistent approach for proactively and reactively reducing vulnerabilities in information systems.
Objectives
- Reduce existing risk to sensitive and/or protected information
- Prevent future risk to sensitive and/or protected information
- Increase availability of services
- Restrict access to sensitive and/or protected information to those with a business need to know
- Streamline and expedite patch management
| PROPERTIES | |
|---|---|
| Property | Description |
| Circulation | Internal Use Only |
| Classification | Public |
| Document Owner | Information Security & Privacy Office |
| Next Scheduled Review | 11/01/2024 |
| Effective Date | 11/25/2015 |
APPROVALS | ||
|---|---|---|
| Version | Date | Approved by |
| 1.3 | 11/25/2015 | Jeff Gassaway |
| 2.0 | 4/26/2016 | Jeff Gassaway |
| 2.1 | 11/3/2023 | Jeff Gassaway |
Scope
UNM Enterprise Information Technologies
- Any system that is administered or owned by UNM Information Technologies or;
- Any system that is owned by UNM, that is intended to communicate with UNM Information Technologies systems
Non-enterprise UNM Information Systems
Departments that host information systems may have vulnerability management program components that are more restrictive than this, but not less.
Departments that are not customers of UNM IT managed services may request ad-hoc vulnerability scanning, reporting, and remediation plans, for a fee. The Information Security & Privacy Office will request prompt remediation if vulnerabilities are discovered in departmental information systems that can impact UNM IT systems, or if those vulnerabilities cause immediate or substantial risk to information for which the institution is responsible.
Failure to adequately safeguard information or failure to appropriately respond to security events and incidents in a timely manner may result in downtime and incident response and remediation fees, as specified by IT SLAs.
Contracted Cloud Services & Service Providers
UNM staff must ensure that sensitive information for which the university is responsible is adequately safeguarded. The Information Security & Privacy Office will review vendor vulnerability management practices for third party services that involve sensitive or protected information.
Vulnerability Management Lifecycle Overview
Vulnerability management is the cyclic and continuous process of identifying and remediating vulnerabilities in information systems. Addressing these vulnerabilities in a timely manner greatly reduces risk to the confidentiality, integrity, and availability of information stored, processed, or transmitted by those information systems. Any system can have vulnerabilities that are either inherent to the type of system, it's software versions, or it's configuration. Operating systems, applications, firmware, and other software constructs which enable information systems to do their jobs can be vulnerable in countless ways.
Many organizations, including universities and colleges, have experienced breaches of various scales. No matter how large or small, data breaches have costly consequences such as lost revenue, diverted revenue, customer harm, and reputational harm. Effective vulnerability management can identify risks and threats to information by preventing breaches, increasing up- time, and building customer trust.
Over time, the vulnerability landscape evolves, thus the tools and techniques used to identify and resolve vulnerabilities must do so too. New controls must be enabled to address new vulnerabilities, while many controls must stay in place for long periods of time in order to prevent attacks against legacy vulnerabilities.


Discover
Systems within the UNM IT Data Center must be scanned periodically for the presence of vulnerabilities (see Appendix: A). Furthermore, after significant changes occur to systems or infrastructure, scans must be conducted to ensure that the changes did not introduce new or unknown vulnerabilities. Each scan will be tailored to the system or group of systems so that the results are as accurate as possible and to ensure the scan is as minimally impactful as possible.
When vulnerabilities are disclosed to UNM -- that is, a third party provides the institution of knowledge that a given vulnerability exists in a UNM system -- analysts and/or administrators will validate the finding with available tools prior to implementing a remediation plan.
Prioritize
Vulnerabilities are prioritized based on their potential impact if successfully exploited and on the likelihood of exploit. In other words, the vulnerabilities that pose the highest risk in a given situation are to be remediated first.
Factors used to calculate the likelihood of a particular vulnerability being exploited include: assumed attacker skill-level, motive and opportunity; UNM service design, and infrastructure configuration; sensitivity of information stored or accessed by or through the infrastructure, and ease of discovery or exploitation of a given vulnerability.
On occasion, simultaneous vulnerability discoveries will be made. Depending on the circumstances, and value of an asset, certain vulnerabilities take precedence over others. Most tools used to discover vulnerabilities include criticality scores based on Common Vulnerability and Exposures (CVE) scores. These scores are a reasonable measure of how "bad" a given vulnerability is. However, these scores do not account for details such as the mission criticality of the system, existing compensating controls, or the sensitivity of the data stored, transmitted or processed by that system. Staff in the Information Security & Privacy Office will take these variables into account when determining the priority that vulnerabilities need to be acted upon.
The Information Security & Privacy Office defines severity:
Critical and High
This class of vulnerability poses the highest risk to the confidentiality, integrity, and availability of information or systems. These vulnerabilities can have the most negative impact on business operations.
- Difficulty to exploit may be low
- Likelihood of exploit is very high
- Successful attack can lead to complete breach of confidentiality, integrity, and / or availability of information,
- Immediate response is recommended
Medium
This class of vulnerability poses moderate risk to the confidentiality, integrity, and availability of information or systems.
- Difficulty to exploit may be medium to high
- Likelihood of exploit is medium to high
- Successful attack can lead to partial breach of confidentiality, integrity, or availability of information
- Immediate response may not be necessary, however, it is best practice to remediate all "medium" vulnerabilities
Low
This class of vulnerability may pose risk to the confidentiality, integrity, and availability, of information or systems.
- Difficulty to exploit may be high
- Likelihood of exploit is medium to low
- Successful attack can lead to partial breach of confidentiality, integrity, or availability of information
- Immediate response may not be necessary, however, existing compensating controls, upcoming patch releases, and the specific environment should be evaluated to determine residual risk
See Appendix: C for CVE calculations.
See Appendix: D for required remediation timeframes and exception levels.
Plan
Each team responsible for maintaining information systems must create a workflow or process that fits the specific environment, toolsets, and application that describes how they will apply patches to vulnerabilities. Any non-standard workflow or process must meet the intent and rigor of this program component.
The Information Security & Privacy team must approve any workflow or process prior to implementation.
See Appendix: B for required patch workflow standard.
Mitigate
Mitigation will occur within an appropriate timeframe for the criticality of the vulnerability. Mitigation strategies should be prioritized in the following order:
First, follow vendor / manufacturer recommendation, for example:
- Implement patch
- Change configuration
Next, implement compensating control
If vendor / manufacturer has no recommendation, patch, hotfix, etc. OR there are documented constraints , an appropriate compensating control meeting criteria defined in Definitions should be implemented
Follow risk acceptance process
An exception may be sought depending upon the criticality of the vulnerability. See Appendix D
See Appendix: D for required remediation timeframes and exception levels.
Validate
Validation is a crucial stage in vulnerability management that aims to objectively determine whether a patch, configuration change, or compensating control is performing the intended function. Validation will occur during periodic scanning, however, ad-hoc validation should be conducted in circumstances where appropriate, such as after implementing a patch or compensating control. Any team maintaining information systems may request that the Information Security & Privacy Office conduct validation testing or scanning.
Definitions
Availability
For any information system to serve its purpose, the information must be available when it is needed by those who have a business need to know. This means that the computing systems used to store and process the information, the security controls used to protect it, and the communication channels used to access it must be functioning correctly. High availability systems aim to remain available at all times, preventing service disruptions due to power outages, hardware failures, and system upgrades. Ensuring availability also involves preventing denial-of-service attacks, such as a flood of incoming messages to the target system essentially forcing it to shut down.
Confidentiality
A concept that applies to data that must be held in confidence and describes that status or degree of protection that must be provided for such data about individuals as well as organizations and systems.
Compensating Control
Compensating controls are controls that are not identical to the original control, but that meet the intent and rigor of the original control. Compensating Controls may be considered when an entity cannot meet a requirement explicitly as stated or mitigate a vulnerability effectively due to legitimate technical or documented business constraints, but has sufficiently mitigated the risk associated with the requirement through implementation of other controls.
Critical Infrastructure
Any system, set of systems, or resource that is critical to the mission of the University and any device that is running a mission-critical service for the University or a device that is considered mission critical based on the dependency for business functions.
CVSS
The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. CVSS consists of three metric groups: Base, Temporal, and Environmental. The Base group represents the intrinsic qualities of a vulnerability, the Temporal group reflects the characteristics of a vulnerability that change over time, and the Environmental group represents the characteristics of a vulnerability that are unique to a user's environment. The Base metrics produce a score ranging from 0 to 10, which can then be modified by scoring the Temporal and Environmental metrics.
Exploit
An exploit (from the English verb to exploit, meaning "using something to one's own advantage") is a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in order to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic (usually computerized).
External Scans
Vulnerability scans conducted by a scanner residing on a different network from its targets. Usually, an external scan is conducted via the ingress point of a network. In other words, external scans originate from the external Internet connection into a trusted network. External scans provide a view of the network that attackers see.
Integrity
In information security, data integrity means maintaining and assuring the accuracy and consistency of data over its entire life cycle. This means that data cannot be modified in an unauthorized or undetected manner. Information security systems typically provide message integrity in addition to data confidentiality.
Internal Scans
Vulnerability scans conducted by a scanner within the same network as its targets. Internal scans usually provide a higher level of visibility due to the fewer number of security controls they must traverse. Internal scans are critical in determining baseline risk, prior to calculating the residual risk which includes implemented security controls.
Penetration Tests
Penetration testing is the process of attempting to gain unauthorized access to resources without knowledge of usernames, passwords and other normal means of access Penetration tests are conducted with prior authorization from an organization, in contrast to an unauthorized attack.
Residual Risk
Portion of risk accepted by management that remains after security measures have been applied.
Risk
A measure of the extent to which an entity is threatened by a potential circumstance or event, and typically a function of: a) the adverse impacts that would arise if the circumstance or event occurs; and b) the likelihood of the occurrence of that risk.
Information system-related security risks are those risks that arise from the loss of confidentiality, integrity, or availability of information or information systems and reflect the potential adverse impacts to organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, and other organizations.


Threat
Any circumstance or event with the potential to adversely impact organizational operations (including mission, functions, image, or reputation), organizational assets, individuals, or other organizations through an information system via unauthorized access, destruction, disclosure, modification of information, and/or denial of service.
Vulnerability
A weakness in information systems, security procedures, internal controls, or implementations that could be exploited or triggered by a threat source.
Vulnerability Scanner
A vulnerability scanner is a computer program designed to assess computers, computer systems, networks or applications for weaknesses.
Vulnerability Management
The cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities.
Appendix A: Scan Schedule
| Device Group | Scan Frequency | Credentialed |
|---|---|---|
| Internal Scans | ||
| UNM Enterprise Information Systems Ex. All devices and hosts in the UNM IT Data Center and all Enterprise Network equipment | Minimum of every 30 days | Combination |
| Non-Enterprise UNM Information Systems Ex. Information Systems managed by non-enterprise staff | Minimum of every 30 days, resource dependent | Combination, as appropriate, resource dependent |
| UNM Networks All devices and hosts connected to the UNM IT Network | Every 180 days, as appropriate, resource dependent | No |
| External Scans | ||
| UNM Enterprise Information Systems Ex. All devices and hosts in the UNM IT Data Center and all Enterprise Network equipment | Quarterly, on demand as needed | No |
| Internally Provided Penetration Testing | ||
| External Facing Services | On demand as needed | Combination |
| Internal Facing Services | On demand as needed | Combination |
| Third-Party Provided Penetration Testing | ||
| Critical Enterprise Systems | Annually, on demand as needed / required | Combination |
| Regulated Enterprise Systems | Annually, on demand as needed / required | Combination |
| Regulated Non-Enterprise Systems | On demand as needed / required | Combination |
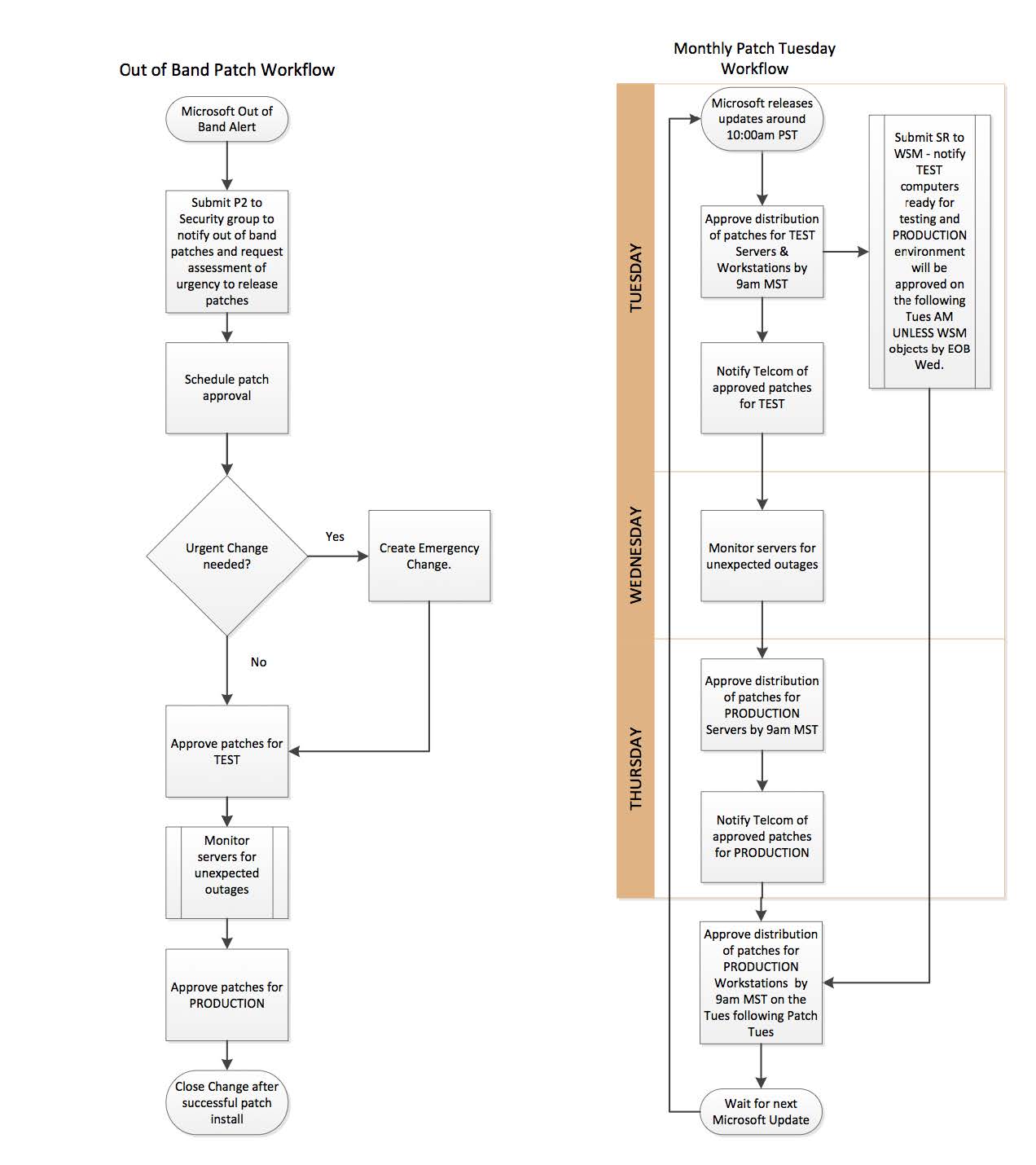
Appendix B: Sample Patch Workflow

Appendix C: CVE Calculations Example
This is an example Common Vulnerability and Exposures (CVE) score. Using the online calculator, metrics were selected to demonstrate how CVE scores are determined. The higher the score, the greater the impact. In this example the metrics are set as:
- Network exploitable, medium difficulty, and no authentication required
- Complete confidentiality impact, partial integrity impact, partial availability impact


Appendix D: Remediation Timeframe
| Criticality | After detection, remediation required within | Exception Approval |
|---|---|---|
| Critical | 7 calendar days | ISPO, CIO, or Data Owner |
| High | 14 calendar days | ISPO, CIO, or Data Owner |
| Medium | 30 calendar days | ISPO, CIO, or Data Owner |
| Low | 90 calendar days | ISPO, Team Lead or Service Owner |
| REVISION HISTORY | |||
|---|---|---|---|
| Version | Date | Description of Changes | Revised by |
| 2.0 | 4/26/2016 | Formatting, verbiage update to include application vulnerabilities | Lucas Walker |
| 2.1 | 11/3/2023 | Updated classification, logo, and language in Purpose section. Added language pertaining to the Critical severity category. | Harold Chang |
If you have questions or would like to provide feedback regarding this document, please use ServiceNow to submit a request to ensure your question or feedback is received and tracked.
