Awareness Management
Purpose
The University of New Mexico is committed to protecting the information with which it is entrusted. This component of the UNM Information Security Program aligns with the National Institute of Standards and Technology (NIST) Special Publication (SP) Series and Frameworks. This Awareness Management program component describes how UNM helps minimize risks to the confidentiality, integrity, and availability of information for which UNM is responsible. This Awareness Management program component accomplishes this by providing UNM with a standard and consistent approach for building and maintaining effective information security awareness activities and resources.
The purpose of this document is to establish guidance for building and maintaining Information Security Awareness at The University of New Mexico (UNM). This document describes UNM's standard awareness management program activities and resource. The goal of this document is to be descriptive rather than prescriptive. Various combinations of strategies may be employed to accomplish comprehensive security awareness. As people, process, and technology, and the ways in which technologies are used change, so must the methods of awareness training.
Objectives
- Identify the audience
- Identify roles and responsibilities
- Identify mechanisms
- Establish methodologies
| PROPERTIES | |
|---|---|
| Property | Description |
| Circulation | Internal Use Only |
| Classification | Public |
| Document Owner | Information Security & Privacy Office |
| Next Scheduled Review | 11/01/2024 |
| Effective Date | 2/24/2017 |
| APPROVALS | ||
|---|---|---|
| Version | Date | Approved by |
| 1.0 | 2/23/2017 | Jeff Gassaway |
| 1.1 | 11/03/2023 | Jeff Gassaway |
Audience
The entire UNM community must be engaged at some level to promote awareness of information security principles. A strong information security program cannot be put in place without significant attention given to training users on information security policy, procedures, and techniques, as well as the various management, operational, and technical controls necessary and available to secure information systems.
Additionally, those in the Institution who manage information systems and information technology infrastructure need to have the necessary knowledge to carry out their assigned duties effectively. Failure to give sufficient attention to the area of information security training puts an enterprise at great risk because security of institution resources is as much a human issue as it is a technology issue.
The success of an organization's information security awareness and training program, and that of the overall information security program, depend on the ability of the community to work toward a common goal of protecting the organization's information and technology resources.
Overview 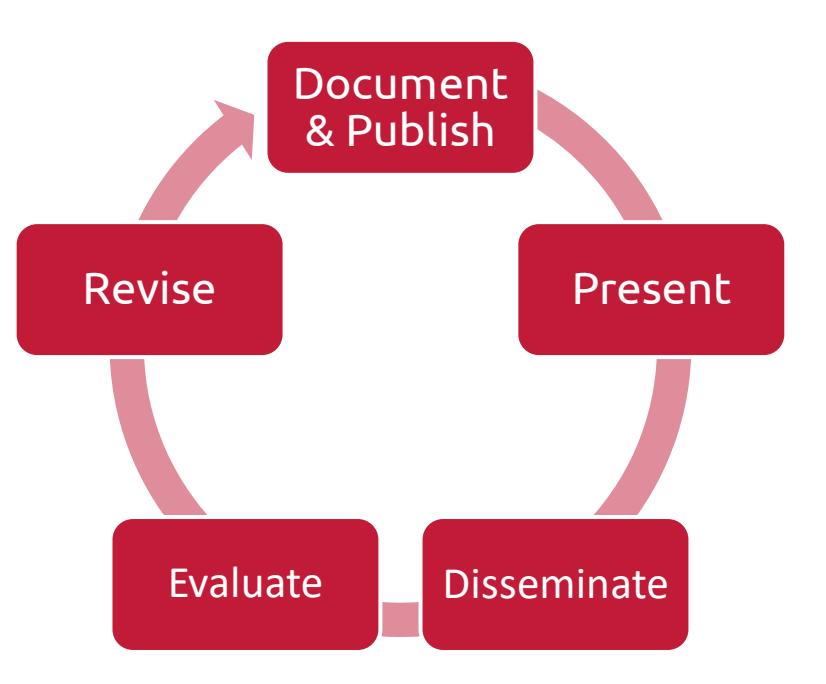
Building and fostering security awareness is a cyclic and continuous process. UNM cannot protect the confidentiality, integrity, and availability of information in today's highly networked systems environment without ensuring that all people involved in using and managing information systems: a) understand their roles and responsibilities related to the organizational mission; b) understand the organization's information security policy, procedures, and practices; and c) have at least adequate knowledge of the various management, operational, and technical controls required and available to protect the information systems for which they are responsible.
The "people factor"- not technology- is key to providing an adequate and appropriate level of security. If people are the key, but are also a weak link, adequate attention must be paid to this "asset." A robust and enterprise wide awareness and training program is paramount to ensuring that people understand their information security responsibilities, organizational policies, and how to properly use and protect the information entrusted to them.
A successful information security awareness program consists of: 1) developing information security policy that reflects business needs tempered by known risks; 2) informing users of their security responsibilities, as documented in institutional security policy and procedures; and 3) establishing processes for monitoring and reviewing the program.
An effective security awareness exercise explains proper rules of behavior for the use of institutional information systems and information. The program communicates security policies and procedures that need to be followed. This must precede and lay the basis for any sanctions imposed due to noncompliance. Users first should be informed of the expectations. Accountability must be derived from a fully informed, well-trained, and aware workforce.
Document & Publish
The first step of the awareness cycle is documentation of knowledge after it has been aggregated from legislation, regulation, contractual obligations, industry best-practice, lessons learned, etc. and formatted appropriately for the respective audience. In the context of this Awareness Management Component of the Institution's Information Security Program, this step is generally conducted by the Information Security & Privacy Officer, ISPO staff, Office of University Council, UNM leadership, and/or other administrative bodies within the Institution.
Examples of output:
- Policies
- Standard Operating Procedures (SOPs)
- Informational Web Pages
- Mandatory Training
- Documentation
- Standards
- Guidelines
Information security awareness materials should be tailored to the audience and communication channel for example, the content in an electronic bulletin may be different than content in an instructor-led training seminar, even though both have the same underlying message. The communication channel used should match the audience receiving the training content and the type of content, as well as the content itself.
Dissemination & Awareness Growth
During this stage, existence of policies, procedures, and any other sources of knowledge must be promulgated to the appropriate audiences. By disseminating information security awareness training via multiple communication channels, the organization ensures that personnel are exposed to the same information multiple times in different ways. This greatly improves how people retain the information presented to them. As the community becomes more aware of information security best practices and the rules governing data become more clear, the campus community will collectively protect data better.
Evaluation
ISPO Staff (and others) must constantly evaluate the effectiveness of the awareness program. While empirically determining the efficacy of certain methods may be difficult, certain methods may see higher rates of success as cultures and attitudes toward certain methods change. Furthermore, the quality and validity of any awareness material must be under constant scrutiny.
Revision
Any time new technologies are developed and begin to proliferate in use, new risks are discovered. The UNM community should be made aware of such developments. The growth in Social Media popularity serves as a prime example of this; as new ways of communicating with friends, colleagues, and strangers arose, they brought many risks, among others, to the privacy of the individual. An organization should identify and understand these risks to ensure that its constituents act reasonably and properly.
Roles and Responsibilities
Chief Information Officer (CIO)
Must ensure that:
- Appropriate priority is given to effective information security awareness and training for the workforce
- The institution's information security program is implemented, is well-supported by resources and budget, and is effective
- That the institution has enough sufficiently trained personnel to protect its information systems and technology resources
Information Security & Privacy Officer
The Information Security & Privacy Officer must help ensure that ISPO staff are enabled to access information and resources pertinent to staying current on information security trends and technologies. This individual must also ensure that appropriate resources are allocated in an effort to create or procure awareness content, materials, or trainings.
Must ensure that:
- Awareness and training materials developed are appropriate and timely for the intended audiences
- Awareness and training materials are effectively deployed to reach the intended audience
- Users and managers have an effective way to provide feedback on the awareness and training materials and their presentation
- Awareness and training materials are reviewed periodically and updated when necessary
ISPO Staff
ISPO Staff must stay current on information security trends and technology. They must also continually evaluate the effectiveness and appropriateness of awareness measures. ISPO Staff will frequently provide trainings, briefings, presentations, or event staffing for awareness exercises. In addition to providing a presence during these exercises, ISPO Staff may be tasked with creating or procuring new content, topics, or materials.
Others
Faculty, students, staff, and guests consuming information security awareness training and materials are encouraged to participate and provide feedback.
Users are the largest audience in any organization and are the single most important group of people who can help to reduce unintentional errors and vulnerabilities. Users may include employees, contractors, foreign or domestic guest researchers, other Institutional personnel, visitors, guests, and other collaborators or associates requiring access.
Users must:
- Understand and comply with institutional information security policies and procedures
- Be appropriately trained in the rules of behavior for the systems and applications to which they have access
- Collaborate with their management to meet training needs
- Be aware of actions they can take to better protect the institution's information. These actions include, but are not limited to: proper password usage, data backup, proper antivirus protection, reporting any suspected information security incidents or violations of information security policy, and following rules established to avoid social engineering attacks and rules to deter the spread of malware.
Information Security Awareness Depth
Establishing a minimum level of information security awareness for all personnel can be the foundation of the information security awareness program.
Security Awareness throughout the Organization
An effective information security awareness program targets the delivery of relevant materials to the appropriate audience in a timely and effective manner.
Below are examples of content commonly included in general information security awareness trainings:
- The Institution's information security policy
- Impact of unauthorized access to systems or facilities
- Importance of strong passwords
- E-mail best practices
- Best practices for working remotely
- Avoiding malicious software
- Web browsing best practices (Internet safety)
- Mobile device security
- Social media best practices
- How to identify and report a potential information security incident and who to report it to
- Protecting against social engineering attacks
- In Person physical access
- Phone caller ID spoofing
- E-mail phishing, spear phishing, e-mail address spoofing
- Instant Messaging
- Physical security
- Shoulder surfing
- Dumpster diving
- Where to get additional information
- See also: "Appendix C: Potential Awareness Topics"
Appropriate trainings and awareness materials shall be provided to those in specialized roles (data owners, data stewards, procurement officers, system administrators, etc.) and management.

Appendix A: Potential Opportunities for Outreach
Staff Outreach Opportunities
New Employee Orientation (NEO)
NEO is an excellent opportunity to engage new and returning staff, however, it is a time when these staff are receiving a multitude of information. Typically, this is a time to announce who and what the Information Security & Privacy Office (ISPO) is, how to contact the ISPO, and when to do so. Consider the following:
- Keep it brief
- Have a pertinent message
- Minimize handouts
Staff Council
Staff Council meetings can be a channel to reach out to staff grade representatives. In addition to guiding discussion points, reaching out directly to Council Members can often help disseminate information about important or relevant information security issues.
Tech Days
This event gives UNM's faculty and staff (and to a lesser degree, students) an opportunity to learn about technologies on campus and participate in discussions of the current state of technology and future innovations at UNM which makes it an excellent avenue to discuss information security concepts as they relate directly to the technology at UNM.
Faculty Outreach Opportunities
New Faculty Orientation (NFO)
NFO is an excellent opportunity to engage new and returning faculty, however, it is a time when faculty are receiving a multitude of information. Typically, this is a time to announce who and what the Information Security & Privacy Office (ISPO) is, how to contact the ISPO, and when to. Consider the following:
- Keep it brief
- Have a pertinent message
- Minimize handouts
Student Outreach Opportunities
New Student Orientation (NSO)
NSO is an excellent opportunity to engage new and returning students, however, it is a time when these students are receiving a multitude of information. Typically, this is a time to announce who and what the Information Security & Privacy Office (ISPO) is, how to contact the ISPO, and when to. Consider the following:
- Keep it brief
- Have a pertinent message
- Minimize handouts
Security Days
This event gives UNM's students (but also faculty, staff, and guests) an opportunity to learn about information security and privacy concepts and participate in discussions of the current state of information security at UNM which makes it an excellent avenue to discuss information security concepts.
Student Groups
- Resident Advisors
- GPSA
Contractor & Guest Outreach Opportunities
In the case of contractors and guests, awareness opportunities can be slim. However, good security marketing can be achieved via login banners, newsletters, access request forms, etc.
Appendix B: Recommendations for Outreach Methods
Email should be used sparingly, as UNM affiliates typically receive numerous emails daily. When utilizing email, follow the below precautions:
- Avoid hyperlinks
- Avoid HTML or other rich content
- Keep it concise
Often, email awareness content is the result of an ISPO action, such as an account lock, a malicious email incident response, or an information security advisory. The ISPO may interject awareness materials into these communications.
Events
Events should be inviting to students, faculty, staff, and guests. Content should be provided in an engaging and informative manner. Event staff should always decline to answer questions they don't have an answer.
Interactive Video & Non-interactive Video
Video presentations should be modern in content and videography. Video content should, in general, be a component of other training materials such as self-guided learning modules.
Knowledgebase
Knowledge bases such as FastInfo, should contain information security and privacy related content including best practices, standard operating procedures, etc.
Presentations
Presentations should always be pertinent and timely. When possible, have guest subject matter experts present. Presentation length should be minimized to assure audience attentiveness.
Printed Material
Keeping up-to-date printed material can be challenging. In addition, consider the following:
- Keep it accurate
- Keep it pertinent
- Adhere to UNM marketing standards
- Adhere to contemporary graphic design norms
Policy
UNM Policies are foundational in creating a point of reference for information security and privacy related issues. UNM Policies that relate to information security and privacy should be written to withstand the test of time to assure a long-lasting document.
Social Engineering Exercises
Social Engineering exercises shall be approved by the Information Security & Privacy Officer. For more information, see "Appendix E: Social Engineering Exercises."
Web Content
Consider the following:
- Keep it current
- Keep it accurate
- Keep it pertinent
- Adhere to UNM marketing standards
- Adhere to contemporary graphic design norms
Appendix C: Potential Awareness Topics 1
A significant number of topics can be mentioned and briefly discussed in any awareness session or campaign. Topics may include:
- Password usage and management including creation, frequency of changes, and protection
- Protection from viruses, worms, Trojan horses, and other malicious code scanning, updating definitions
- Policy implications of noncompliance
- Unknown e-mail/attachments
- Web usage allowed versus prohibited; monitoring of user activity
- Spam
- Data backup and storage centralized or decentralized approach
- Social engineering
- Incident response contact whom? "What do I do?"
- Shoulder surfing
- Changes in system environment increases in risks to systems and data (e.g., water, fire, dust or dirt, physical access)
- Inventory and property transfer identify responsible organization and user responsibilities (e.g., media sanitization)
- Personal use and gain issues systems at work and home
- Handheld device security issues address both physical and wireless security issues
- Use of encryption and the transmission of sensitive/confidential information over the Internet address agency policy, procedures, and technical contact for assistance
- Laptop security while on travel address both physical and information security issues
- Personally owned systems and software at work state whether allowed or not (e.g., copyrights)
- Timely application of system patches part of configuration management
- Software license restriction issues address when copies are allowed and not allowed
- Supported/allowed software on organization systems part of configuration management
- Access control issues address least privilege and separation of duties
- Individual accountability explain what this means in the organization
- Use of acknowledgement statements passwords, access to systems and data, personal use and gain 18 A thorough discussion of topics, organized as management, operational, and technical controls, can be found in NIST Special Publications 800-12, 800-18, and 800-26. 24 NIST Special Publication 800-50
- Visitor control and physical access to spaces discuss applicable physical security policy and procedures, e.g., challenge strangers, report unusual activity
- Desktop security discuss use of screensavers, restricting visitors' view of information on screen (preventing/limiting "shoulder surfing"), battery backup devices, allowed access to systems
- Protect information subject to confidentiality concerns in systems, archived, on backup media, in hardcopy form, and until destroyed
- E-mail list etiquette attached files and other rules.
1 Source : http://csrc.nist.gov/publications/nistpubs/800-50/NIST-SP800-50.pdf
Appendix D: Recommended Awareness Events
| Event | Frequency | Target Audience |
|---|---|---|
| Security Days | Once Per Semester | Students, staff, faculty |
| Tech Days | Annually | Faculty and staff |
| Cyber Infrastructure Day | Annually | Faculty, researchers, staff, and students |
| Once Per Semester | All | |
| Presentations | By Request | Any |
| NEO, NFO, NSO | By Request | Any |
| Staff & Faculty Required Training | Annual | All |
| Targeted Briefings | Annually | IT Applications Team |
| Annually | IT Classroom Technologies | |
| Annually | IT Customer Support Services | |
| Annually | IT Networks | |
| Annually | IT Platforms | |
| Quarterly | IT Town Hall |
Appendix E: Social Engineering Exercises 2
A Social Engineering Penetration Test is designed to simulate attacks that adversaries will use to breach UNM's safeguards. Social engineering, in the context of information security, refers to psychological manipulation of people into performing actions or divulging confidential information. UNM ISPO may engage a trusted third-party to perform these tests or conduct them internally. Any social engineering exercise conducted will be done so in strict adherence to internal SOPs. The primary difference between a simulated and a real adversary are the tester's ethical boundaries. The ISPO expects that any third-party tester and/or internal tester conducting social engineering exercises does so in accordance with a do no harm principle.
Email Vector
Phishing is defined as the "practice of sending emails appearing to be from reputable sources with the goal of influencing or gaining personal information," (Hadnagy & Fincher). Phishing can involve an attachment within an email that loads malware onto a computer or a link to an illegitimate website that can trick an individual into handing over personal information. There are many different forms of attack that are commonly used via phishing. One key to phishing is for the attacker to appear to be something/someone they are not, which ties into the topic of impersonation as well.
Telephone Vector
Vishing is defined as the "practice of eliciting information or attempting to influence action via the telephone." Similar to phishing, the goal of vishing is to obtain valuable information that could contribute to the direct compromise of an organization by exploiting people's willingness to help. Attackers can "spoof", or forge, their outgoing phone number and pose as an authority figure, technician or fellow employee to obtain sensitive information that could lead to the compromise of an organization. Some attackers may use voice changers to conceal identity. Vishing has proven to be one of the most successful methods of gaining information needed to breach an organization. Employee ID numbers, social security numbers, user credentials, home address or any information about the technology or processes a company uses can be considered a success. This information can then be used for further information gathering, or to impersonate an organization's employee, vendor or partner to successfully breach an organization or gain access to a specific customer's account.
Physical Vector
There are a variety of physical methods for information gathering; some require very little equipment and others involve high-tech gear to properly pull them off. The one thing these methods have in common is that they cannot be done from a remote location. A tester has to be on-site and in-person. This means that pretexting, the principles of influence, and other psychological factors are typically necessary to successfully utilize these methods. No one source of information is the leading method to use nor is one method alone likely to give you enough data to secure your best chances for success.
2 Reference: http://www.social-engineer.org/framework/
| REVISION HISTORY | |||
|---|---|---|---|
| Version | Date | Description of Changes | Revised by |
| V1.1 | 11/03/2023 | Updated logo, classification, and language in Purpose section | Harold Chang |
If you have questions or would like to provide feedback regarding this document, please use ServiceNow to submit a request to ensure your question or feedback is received and tracked.
